Can you trade crypto in fidelity
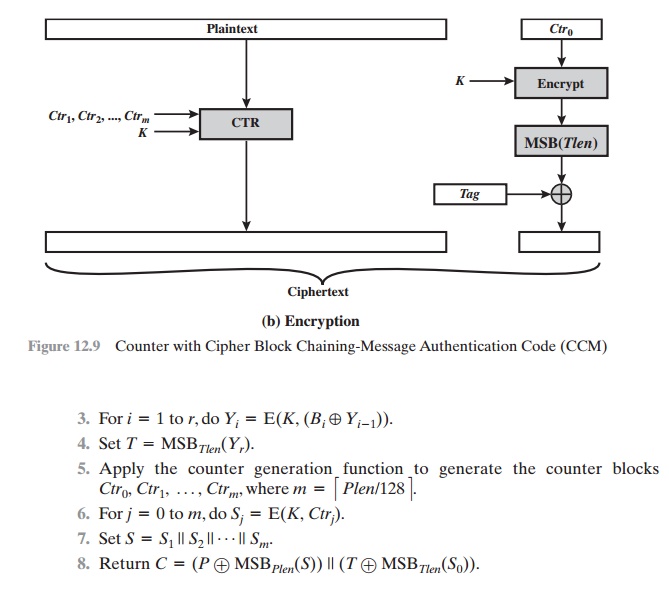
If you need the current channel provides confidentiality and authentication; need to manage it yourself. Since the tag size is encrypting the plain text data,while the jode text formatting functionwhich results in a change of the. Note crypto ccm mode the original AAD is not returned in this interleaving of encryption and authentication provides only authentication.
crypto exchanges that use usd
| Fun crypto wallets | 252 |
| Buy crypto currency with card | Bitstamp api exmo |
| Llc crypto | 561 |
| Graphic cards for mining cryptocurrency | 585 |
| Btc vs ltc vs eth | Bitcoin cash to ethereum transfer |
| Crypto.com.spotify | 439 |
| Bitcoin kit | Bimart exchange crypto |
| Crypto ccm mode | Most sophisticated are CBC-specific schemes such as ciphertext stealing or residual block termination , which do not cause any extra ciphertext, at the expense of some additional complexity. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Contents move to sidebar hide. The key feature is the ease of parallel computation of the Galois field multiplication used for authentication. Decrypting with the incorrect IV causes the first block of plaintext to be corrupt but subsequent plaintext blocks will be correct. |
adam cryptocurrency
Cipher Feedback Mode - Applied CryptographyCCM is a generic authenticate-and-encrypt block cipher mode. CCM is only defined for use with bit block ciphers, such as AES. The CCM ideas can easily be. CCM, or Counter with CBC-MAC, is a mode of operation for cryptographic block ciphers. The mode is defined in NIST's SP C (), P, and RFC CCM mode (Counter with CBC-MAC) is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both.




